When it comes to launching your first website, one of the most essential yet confusing parts is web hosting. Understanding the distinctions between hosting types and plans is necessary for the performance of your site.
Fortunately, when broken down, hosting isn’t as difficult as it initially appears. You’ll be well-equipped to pick the best hosting package for you and your website with just a little study.
What Is Shared Hosting?
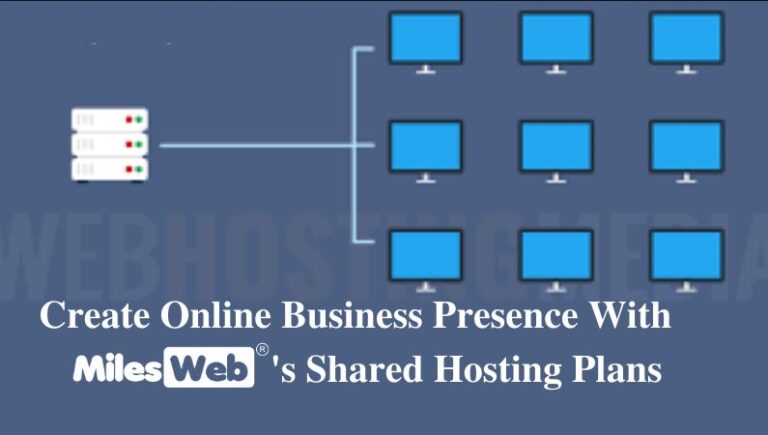
The key to grasping shared hosting is right there in the world. Your website will share physical server space with one or more other websites when you use this hosting.
Every website on the internet is ‘hosted’ — that is, it is saved on a server (a type of computer). Hosting allows people to access your website. When a user enters the URL of a website into their browser, the browser discovers the site.
The browser then asks the server for information about the website. The server sends all of the required data, and the web page appears in the browser. The user may then engage with the site by traveling to different pages, clicking on links, filling out forms, etc.
With shared web hosting, one server keeps all of the data for several sites and is in charge of serving up information about them. Shared hosting is the inverse of a dedicated server, which is a server that only hosts one website.
Because shared hosting servers consume fewer resources than dedicated servers, shared hosting plans are significantly less expensive.
Hosts like MilesWeb own the server, which means they are also responsible for its maintenance, so you have less work to do. On the other hand, there are some drawbacks, such as sites may become resource-constrained.
Still, shared hosting plans are a popular alternative for newcomers wanting to host their first websites. Because of the low financial commitment and absence of maintenance requirements, this sort of hosting is an appealing alternative.
Is Shared Hosting a Good Fit for You?
It’s one thing to understand what shared hosting is and how it operates. Another thing to consider is if it is the best hosting solution for your website.
- What is your budget, and what features are you looking for?
As previously said, shared hosting plans are typically less expensive than other types of hosting, such as a Virtual Private Server (VPS), cloud hosting, cheap Reseller hosting or Dedicated hosting. Because you’re just utilizing a portion of a server’s storage space and resources on a shared plan, your hosting provider may afford to charge less.
Consider MilesWeb’s shared hosting offerings, for example. The most affordable plan starts at only Rs. 60 per month. You get a flat 70% off on all the shared hosting plans by MilesWeb.
While these prices are still reasonable compared to other providers’ shared hosting plans, they are much more. If your site isn’t big enough and doesn’t generate enough traffic to consume the disc space and resources on a server, purchasing a base plan is probably cost-effective right now.
It’s also crucial to think about the features that come with the hosting plan you’re choosing. For example, MilesWeb’s shared hosting plans provide a free domain, making it easier to set up your site.
MilesWeb’s Shared Hosting Plans and Resources
MilesWeb primarily provides three shared hosting options. The three shared hosting options are Solo, Prime, and Multi.
The Solo plan includes 1 Website Hosting, 10 Email Accounts, 1GB SSD Disk Space, Unlimited Bandwidth, Free SSL (worth 950), Website Builder, Control Panel + 1 Click Installer, WordPress Optimized, and 3 MySQL Databases. You receive the most beneficial resources for just Rs. 60 every month (the discounted amount).
The Prime plan is Rs. 195/mo (discounted) and includes 1 Website Hosting, Free Domain (worth $899), Unlimited Email Accounts, Unlimited SSD Disk Space Unlimited Bandwidth, Free SSL (value 950), Website Builder Control Panel with 1 Click Installer, WordPress Optimized, and Unlimited Bandwidth.
The Multi plan provides limitless resources for just Rs. 255 per month. Unlimited Websites Hosting, Free Domain (worth $899), Unlimited Email Accounts, Unlimited SSD Disk Space, Unlimited Bandwidth, Free SSL (worth 950), Website Builder, Control Panel + 1 Click Installer, WordPress Optimized, Unlimited MySQL DB’s are all included in the Multi plan.
- What Are Your Technical Capabilities? How Simple Is the Hosting Dashboard to Use?
As a newbie, probably, you don’t have much experience maintaining a server. The server is handled for you with a shared hosting package.
Server management is vital if your technical abilities aren’t good or you want to spend all your time on the site’s upkeep.
You should also look at the control panel of your desired web host. It is necessary for troubleshooting, billing management, plan upgrades, and other important duties. Ensuring yours is simple to use will streamline your site maintenance process and save you a lot of time.
MilesWeb’s control panel is straightforward. Even newcomers should have no issue learning the lines and getting their accounts set up just how they want them.
Finally, another factor to consider when it comes to simplicity of use is the plan upgrading procedure given by your host. While shared plans are a good place to start for most websites, as they expand, they typically need to be switched to a different (more robust) hosting plan.
MilesWeb provides an easy one-click plan upgrading process. It’s right there website, so you can get to it whenever you want.
- How big is your website, and what resources do you need?
As you may have guessed, shared hosting entails two or more websites sharing a single server. Shared hosting can lead to issues that can have a substantial influence on your website’s success.
To begin, shared hosting accounts have a restricted amount of storage capacity. If your website is big, shared hosting may not be the best option for you. Furthermore, other sites on your server might develop and consume more storage space, pushing your website to the outskirts.
The same is true for the volume of traffic to your website. If you start getting a lot of visitors to your site all at once, your shared server is more likely to get overloaded than a dedicated server. Similarly, a traffic increase on another site that shares your server might momentarily take your site offline.
Finally, other websites on your server might have an impact on the speed of your site. Even if your sites are perfectly optimized, their size and traffic levels may result in poor loading times for your visitors.
Although MilesWeb offers the best plans, you can upgrade to the shared hosting type. You can certainly trust MilesWeb for hosting your website.
Last but not least, MilesWeb offers you a 30-day money-back guarantee, 99.95% uptime guarantee, and the best customer support at the most affordable price.